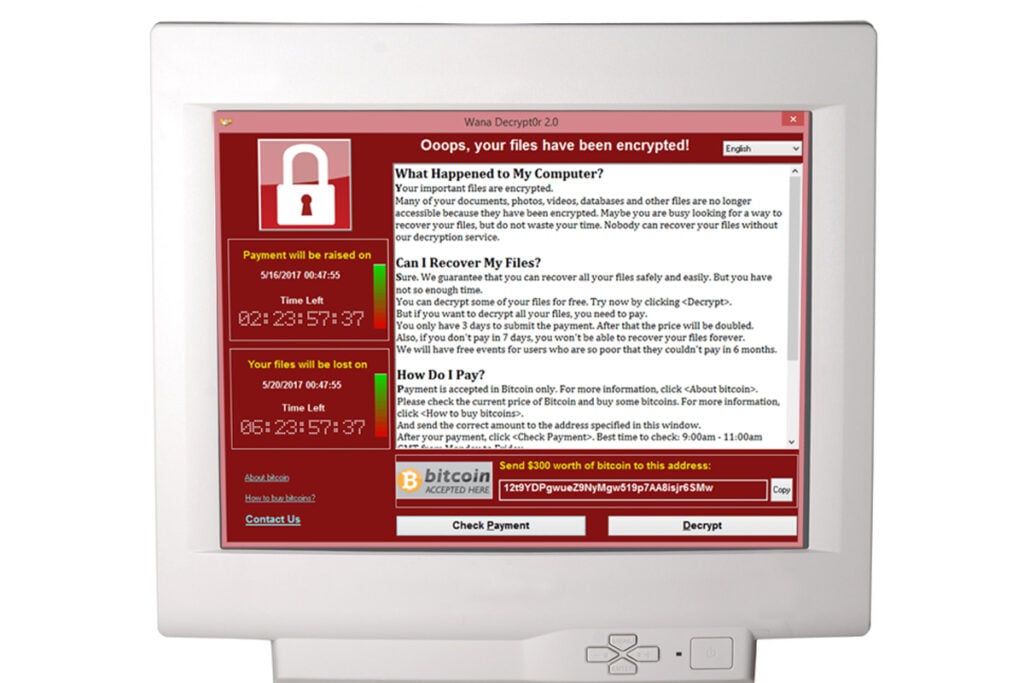
If you walk into your office today, turn on your laptop or PC and everything works as it normally does, you may owe some thanks to someone who goes by the online handle ‘MalwareTech‘. He single handedly was responsible for halting the spread of a ransomware cyber attack that bought down much of the NHS, O2’s parent company Telefonica, FedEx in the US and a host of other businesses and government institutions around the world in at least 99 countries as far afield as Russia and China.
The WannaCry ransomeware infects computers, encrypts most of your useful files, documents and images and then demands $300 to be paid in bitcoins if you want to get your data back. Fail to pay within three days and the blackmailer’s price doubles. Don’t pay within a week and you lose your files forever.
What MalwareTech did was to register a domain name he found buried in the ransomeware source code. Previously the domain hadn’t been registered, but as soon as the ransomeware found the server was live it turned itself off and did no further harm. You can read a full explanation on the MalwareTech blog. The UK’s National Cyber Security Centre were so grateful that they republished MalwareTech’s blog post on their own website.
WannnaCry was particularly malevolent as once it had infected one computer it automatically spread to every other computer it could find on the same network. It’s been suggested that a leaked tool from the USA’s National Security Agency, known as Eternal Blue, was incorporated into the ransomeware to help it spread.
Incidences of employees clicking on infected links, downloading infected documents or visiting infected websites are surprisingly rarer than you might imagine. However it only takes one unsuspecting employee to do so and a cyber attack like WannaCry can spread like wildfire throughout an organisation.
Obviously the best way to protect yourself is to ensure that your employees know not to click on links unless they know the site they’re about to visit. However keeping software up to date with the latest patches and antivirus software is also key. It’s been said that much of the NHS still runs on Windows XP which is now unsupported – Microsoft ceased issuing security patches years ago (in 2014).
Microsoft are “taking the highly unusual step of providing a security update for all customers to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003“. They also stated that “Customers running Windows 10 were not targeted by the attack“.