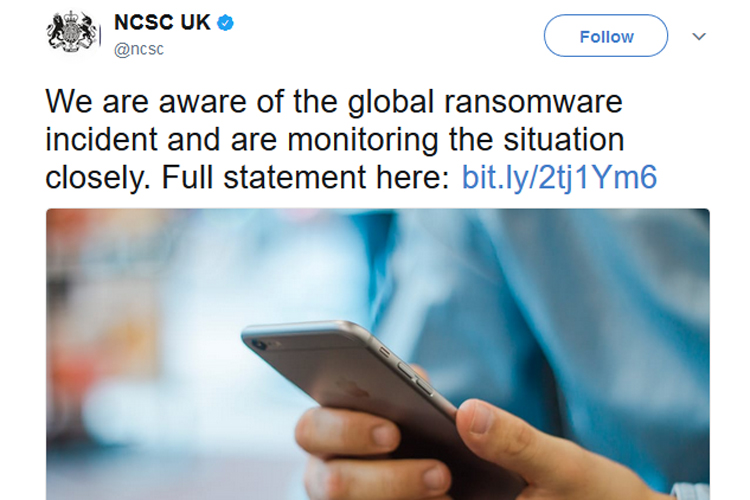
A new ransomware virus has swept across Europe taking down computer systems from companies as large as the Mearsk shipping company and Merck pharmaceutical giant.
It’s a windows based virus and it lacks the firepower of Wannacry which wreaked havoc just a month ago which incorporated EternalBlue, a software believed to have leaked from the NSA. This new ransomware still appears to use EternalBlue but as many systems were patched following Wannacry it’s much less effective.
What makes this new strain appear devastating is that researchers believe it could have initially been spread via automatic software updates to an accounting program widely used in Ukraine – the country the first widespread infections appeared in.
Software updates are designed to come direct from the developer securely to your computer and bypass normal security and firewalls. They basically create an open door into your device and can then install pretty much anything normally having been granted full administrator rights in order to do their job. If you can fake the credentials of a program’s software update routine then that spells real trouble for users of that program.
As with WannaCry, the new ransomware, first thought to be a variant of Petra but now that’s being questioned, demands $300 to be paid by untraceable Bitcoin. Having done this you’re supposed to email the cyber terrorists proof of payment and they’ll give you an unlock code for your computer.
If you’re affected don’t pay
There are any number of reasons not to pay the ransom, but normally some will in desperation as the only way to get their files back and of course success of cyber terrorism simply breeds more incidences in the future. In this case however, paying will be totally futile as they’ll get your money and your files will remain locked.
Ransomware works because the hackers honour their promise to unlock your files, not because they’re honourable, far from it, but because if they didn’t unlock your files there would be no incentive for others to pay up. They rely on their reputation that if the ransom is paid then you get the code.
In this case however, even if you pay the email lifeline you’ll be relying on has been cut off by the ISP. German Posteo who the email account was hosted with cut it off saying ‘We do not tolerate any misuse of our platform‘. The blackmailers can’t access the email inbox and it’s no longer possible to send emails to it. If you pay the ransom all that will happen is the criminals get your Bitcoins, your files are still encrypted and you’re worse off then before – you’re out of pocket an frankly still stuffed with a useless computer and lost data.
As you’d expect the National Cyber Security Centre, are monitoring the situation, but at present have little to say other than their guidance on how to protect yourself which is basically keep software updated with patches (although that might appear to be the root cause of the initial spread in this instance), control code execution (that would have stopped this instance), filter browsing traffic and of course control removable media. Naturally you’ll also want to keep your users educated on the dangers of email attachments and clicking on suspicious links.






One Response
So, from a victim’s point of view, posteo.de is even worse than the ransom-ware crackers, because crackers did provide a way for paying victims, and posteo.de cut it off.
Were I a victim, I’d firewall off 89.146.192.0/18 forever, as a small revenge for leaving me drowning.
And more, I’d consider firewalling posteo.de off anyway, for taking the chance to get some media attention at ransom-ware victims’ expense.