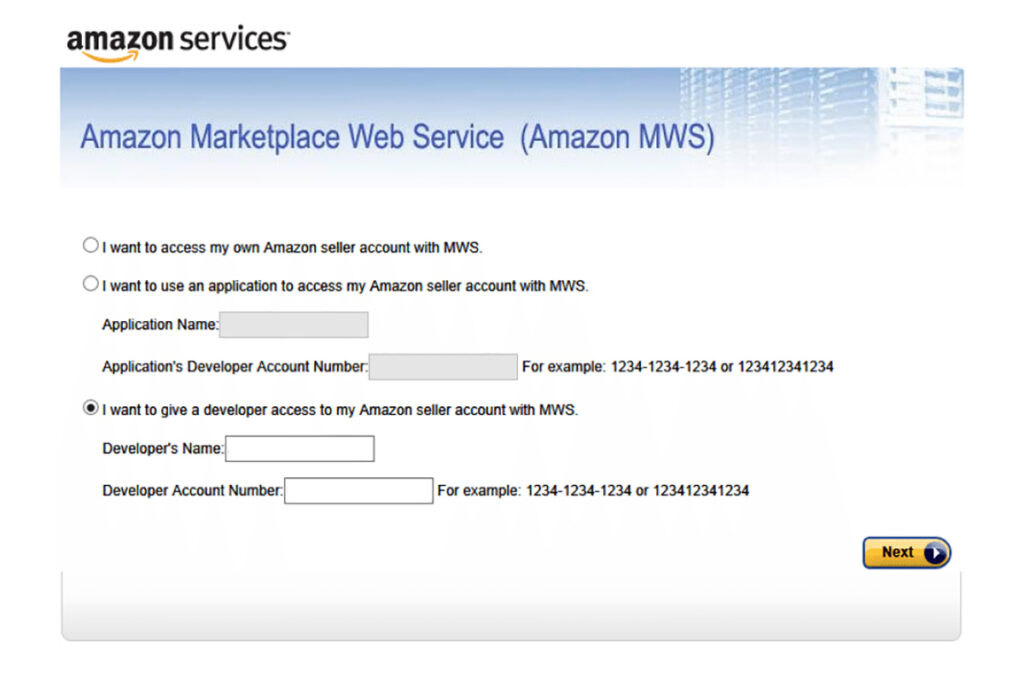
If you use a third party VAT analysis service to handle your VAT for Amazon sales across the EU, your data and that of your customers could be part of around 8 million sales records left exposed on the web and your Amazon MWS credentials should be changed immediately.
A VAT services company appears to have hosted an unsecured database on AWS with millions of sale records including customer names, email addresses, shipping addresses, purchases, and the last four digits of credit card numbers. Also in the database were hundreds of thousands of Amazon Marketplace Web Services (MWS) queries, an MWS authenticaiton token, AWS access key ID, and a secret key.
The Amazon MWS queries and login info could be used to access records from Amazon MWS sales databases. Merchants are advised to change their Amazon MWS credentials (passwords and secret keys) as a precaution. Your Amazon MWS credentials are used to authorise third party apps giving them access to your Amazon marketplace account and so once changed you will need to re-authorise the services you use.
Comparitech’s security research team headed by reknowned security breach finder Bob Diachenko uncovered the database early in February and immediately reported it to Amazon who responded within 24 hours. It is thought to have been unsecured and online for anyone to find for at least 5 days before being removed.
“We were made aware of an issue with a third party developer (who works with a number of Amazon sellers), who appears to have held a database containing information from several different companies, including Amazon. The database was available on the internet for a very short period of time. As soon as we were made aware, we ensured the third party developer took immediate action to remove the database and secure the data. The security of Amazon’s systems was not compromised in any way.”
– Amazon
Subsequent research discovered the owner of the database (not Amazon), although the researchers have decided there is no value in naming and shaming the third party VAT analysis service it belonged to.
“Comparitech elected not to publicly disclose the name of the vendor responsible for the database because it is a legitimate small business. Our intent is to raise awareness and mitigate harm to customers who might be affected, not to punish mistakes. Given that the vast majority of customers are probably not aware their data ever passed through this vendor’s hands, we do not believe there is much to be gained from exposing it.”
– Comparitech
The VAT analysis service collated sales data from Amazon, eBay, Shopify, PayPal, and Stripe to aggregate retailers’ sales data and calculate VAT for different EU countries so it is likely larger merchants who’s sales data was compromised – smaller sellers would not have had the same VAT reporting requirements. However as a single consumer could have made multiple purchases it’s not known how many consumers had their data exposed, let alone how many retailers the transactions related to.
Whilst merchants should update their Amazon MWS credentials, consumers who will be largely unaware that their data could have been compromised are vulnerable to fake phishing emails which could now contain details of authentic transactions. Not only will consumers be unaware that their data has been exposed, but they are highly unlikely even to know that the third party VAT analysis service exists and processes their data on behalf of merchants.