We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept”, you consent to the use of ALL the cookies. However, you may visit "View Preferences" to provide a controlled consent.
The technical storage or access is strictly necessary for the legitimate purpose of enabling the use of a specific service explicitly requested by the subscriber or user, or for the sole purpose of carrying out the transmission of a communication over an electronic communications network.
The technical storage or access is necessary for the legitimate purpose of storing preferences that are not requested by the subscriber or user.
The technical storage or access that is used exclusively for statistical purposes.
The technical storage or access that is used exclusively for anonymous statistical purposes. Without a subpoena, voluntary compliance on the part of your Internet Service Provider, or additional records from a third party, information stored or retrieved for this purpose alone cannot usually be used to identify you.
The technical storage or access is required to create user profiles to send advertising, or to track the user on a website or across several websites for similar marketing purposes.








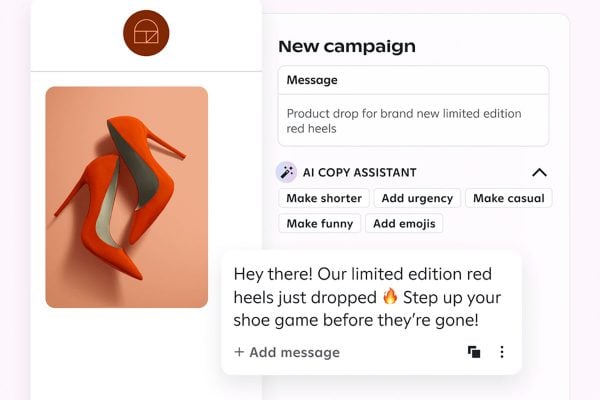
5 Responses
I would really, REALLY like them to address the issue of how one tells them “this is me on a new computer”.
It’s the most bizarre thing have done this year, so far 😆
Surely if you hack someones account you would just change the phone details to your own? verification calls are not normally carried out by people its just a case of the machine acknowledging the receiver has been picked up.
I am obviously missing the point about hackers and what they do with a hacked accounts, why would a hacker list items ? surely you just open your own account? Can someone explain.
Hacker use someone else’s account with good feedback history then list loads of expensive items, usually with email me on xxxxx in the listing, then persuade people to send them payment for the non existent items.
If they set up their own accounts people would be less likely to trust them with no feedback and if they did post load of expensive stuff straight away their auctions would be quickly pulled by ebay.
I wonder what has prompted all of this “security” now? How often does this really happen, is it really one of the top issues that eBay need to resolve?
It’s been announced in India as well now
https://www2.ebay.com/aw/in/200804.shtml#2008-04-16151725